Blogs
Articles and Thoughts
Vision LLMs: Bridging the Gap Between Vision and Language
The field of Artificial Intelligence has undergone remarkable transformations, with innovations spanning natural language processing (NLP) and computer vision.
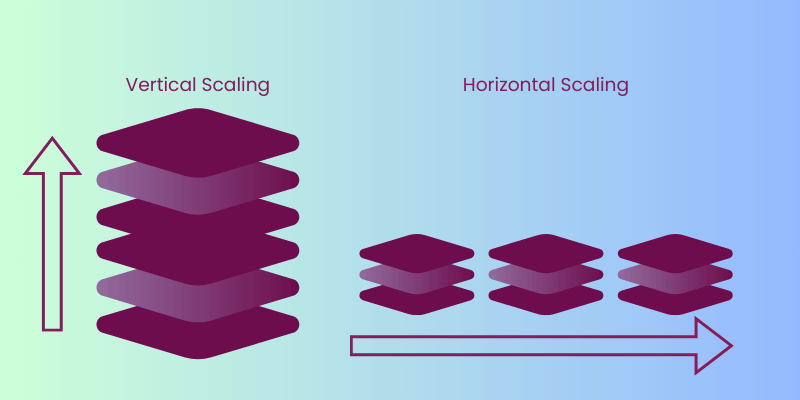
Horizontal Scaling vs. Vertical Scaling: Optimizing Your Infrastructure with AWS and Large Language Models
Imagine your startup is experiencing explosive growth. Your user base is expanding rapidly, and your servers are struggling to keep up with the increasing demand.
Automotive Infotainment Services: Enhancing the In-Car Experience
Automotive infotainment services are a critical part of modern vehicle design, providing a seamless blend of entertainment, communication, and navigation systems.
Graph Neural Networks Demystified: How They Work, their Applications and Essential Tools
Graph Neural Networks (GNNs) are a powerful type of deep learning model designed to handle data in the form of graphs. Unlike traditional methods, which work well with data represented
FPGA Design Services: From System Architecture to Product Testing
Field Programmable Gate Arrays (FPGAs) play a vital role in today's electronics, offering a versatile and reconfigurable platform for a wide range of applications. They find use in various industries,
Harnessing the Power of LLM Evaluation with RAGAS: A Comprehensive Guide
Large Language Models (LLMs) like GPT-4, Llama-2, Llama-3, Mistral, and Phi have changed how we handle, understand and process language. However, evaluating these models is crucial to make sure they
Trapped in the AI Echo Chamber: Unveiling the Pitfalls of Synthetic Data
Artificial Intelligence (AI) is undeniably transforming our world. From personalised recommendations on streaming platforms to life-saving diagnostics in healthcare, AI’s impact is vast and growing.
Top UVM Debugging Hacks that will transform your workflow
Debugging within the Universal Verification Methodology (UVM) framework can often feel like a daunting, time-consuming task. With complex testbenches, identifying and resolving issues can significantly slow down the verification process.
HMI Trends In Android Automotive OS | Part 2
As the automotive industry continues to evolve, the importance of enhanced UI cannot be overlooked. A key aspect of this evolution is integration of games engines and gamification tools into
HMI Trends In Android Automotive OS | Part 1
In the domain of Android Automotive OS (AAOS), Human-Machine Interface (HMI) trends are rapidly evolving to enhance user experiences within automotive environments.
IR Face Detection and Recognition using YOLOv8 and FaceNet
Face recognition technology is an advanced system that uses intricate algorithms and machine learning methods to recognize or authenticate people based on their distinct facial characteristics.
CPU Stress Testing using Random Disturbances
The performance of modern processors has substantially improved by exploiting techniques like out-of-order execution, on-chip caching, speculative execution, prefetching, and thread switching.
Leveraging GenAI and LLMs for Accurate Video Ad Classification
Video advertising is an integral part of the digital marketing ecosystem, playing a crucial role in engaging audiences and driving brand awareness. With the exponential rise of multimedia content
VSLAM Series – Loop Closure Detection
In the third installment of our Visual SLAM series, we delve into the pivotal concept of loop closure.
VSLAM Series – Triangulation & Map Point Creation
The second part of the Visual SLAM blog series discusses one of the key components in visual SLAM: the feature extraction pipeline, which includes triangulation and map point creation. These
VSLAM Series – Feature Extraction & Description Pipeline
This Series of blogs explores the exciting field of Feature based Visual Simultaneous Localization and Mapping (VSLAM). It also discusses the two state-of-the-art algorithms that are widely used in this
Enhancing ISO26262 Functional Safety Validation: Challenges and Best Practices
Functional safety is a vital discipline in engineering, focusing on ensuring system safety in areas impacting human safety or the environment.
Navigating Over-the-Air Updates on Android Automotive OS
From in-vehicle infotainment systems to advanced driver assistance systems (ADAS), OTA updates play a crucial role in keeping automotive software up-to-date and ensuring optimal performance.