- Nesty Mathew
- February 6, 2025
The Right Way to Implement Edge Computing for Your IoT Performance in IT
Introduction
The exponential growth of the Internet of Things (IoT) has transformed the IT landscape, enabling connected devices to gather and share vast amounts of data. However, as the number of IoT devices increases, traditional cloud-centric models face limitations in handling the demand for real-time processing and secure data management. This is where edge computing steps in as a game-changer.
Edge computing involves processing data closer to the source of its generation, reducing reliance on centralized cloud systems. By doing so, it improves performance, enhances data security, and minimizes latency. For organizations leveraging IoT in IT, adopting edge computing ensures faster decision-making and more efficient resource utilization.
Traditional IoT faces several significant challenges that impact its efficiency and reliability. Security remains a major concern, with over 80% of IoT deployments vulnerable to cyberattacks, which have surged by more than 300% in recent years. Scalability is another issue, as nearly 40% of enterprises struggle to manage the rapid expansion of connected devices. Latency also poses a problem, especially in industrial applications, where real-time processing is crucial—yet 50% of such systems experience delays due to cloud dependency. Additionally, power consumption is a growing concern, with 70% of IoT devices running on batteries, leading to frequent maintenance and higher operational costs.
This blog explores the concept of edge computing in IoT, its architecture, advantages, challenges, and implementation strategies for maximizing IT performance.
Understanding Edge Computing
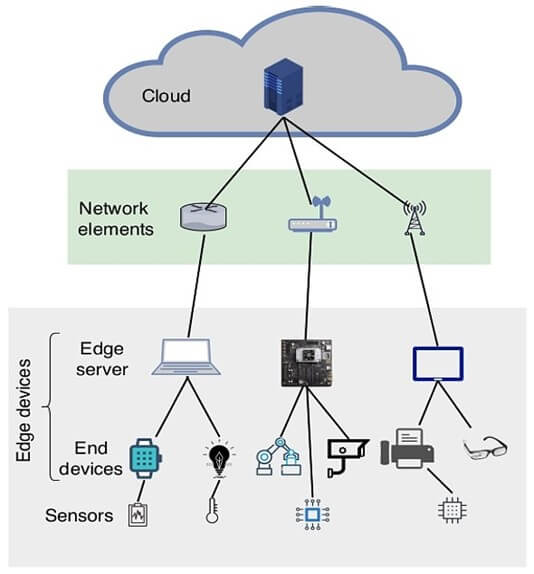
Edge computing is a distributed computing paradigm where data is processed and analyzed near its source, such as on IoT devices or local edge servers. Unlike the traditional cloud model, where data travels to remote servers for processing, edge computing reduces this dependency, enabling real-time actions and decisions.
Software Architecture
In modern edge systems, microservices play a crucial role by breaking applications into smaller, independent components. Each service handles a specific task, making it easier to scale, update, and manage. This modular approach means edge computing systems can handle tasks like data processing or decision-making in isolation. For example, in industrial IoT, an anomaly detection service can be updated or improved without disrupting the rest of the system, ensuring smoother operation and faster response times.
Protocols in Use
For edge computing to work efficiently, devices need to communicate quickly, reliably, and with minimal resource consumption. This is where lightweight messaging protocols like MQTT, CoAP, and AMQP come into play. Each protocol is designed for specific use cases, ensuring seamless data exchange between IoT devices, edge nodes, and cloud servers.
1. MQTT (Message Queuing Telemetry Transport) – Ideal for Low Bandwidth Networks
MQTT is a lightweight, publish-subscribe protocol designed for devices operating in low-bandwidth, high-latency, or unreliable networks.
- Instead of devices directly communicating with each other, MQTT uses a broker that manages messages. Devices publish data to specific topics, and other devices (subscribers) receive updates when new data is published.
- Works efficiently even with limited network availability (e.g., remote sensors in agriculture).
- Minimal power consumption, making it ideal for battery-powered IoT devices.
- Used in industrial automation, smart homes, and connected vehicles.
- Example Use Case: A fleet of smart meters in a smart grid system can use MQTT to send real-time energy consumption data to an edge server for analysis, without overloading the network.
2. CoAP (Constrained Application Protocol) – Best for Low-Power Devices
CoAP is an HTTP-like protocol optimized for lightweight IoT devices that operate on low-power networks (e.g., LoRa, Zigbee, NB-IoT).
- CoAP follows a client-server model, where IoT devices (clients) send requests to edge nodes (servers) and receive responses.
- Consumes very little power, making it perfect for battery-operated sensors.
- Supports multicast communication, reducing network congestion.
- Ideal for environmental monitoring, healthcare wearables, and industrial sensors.
- Example Use Case: A smart irrigation system in agriculture can use CoAP to send soil moisture data to an edge node, which then makes watering decisions without needing a cloud connection.
3. AMQP (Advanced Message Queuing Protocol) – Ensures Reliable Message Delivery
AMQP is a message-oriented protocol designed for secure and reliable data exchange in mission-critical applications.
- AMQP ensures that messages are delivered once and in order, even if network interruptions occur. It also supports message queuing, allowing edge devices to store and forward data when connectivity is restored.
- Guarantees message delivery even in unstable networks.
- Supports transactional messaging, which is crucial for financial services and healthcare systems.
- Used in banking, logistics, and real-time monitoring.
- Example Use Case: In hospital patient monitoring, AMQP ensures that critical health data (like heart rate and oxygen levels) is delivered to doctors without delays or data loss, even if the network is congested.
Algorithms
Edge computing relies on AI-driven machine learning algorithms to process data locally, enabling faster decision-making and reducing cloud dependency. Here are some of the most common algorithms used in edge computing:
1. Anomaly Detection – Identifying Unusual Patterns in Real Time
Anomaly detection algorithms help detect faults, security breaches, or unusual behavior in data streams before they escalate.
- Common algorithms:
- Isolation Forest (IForest): Efficient for detecting anomalies in large datasets by isolating outliers.
- SVM (Support Vector Machine): Classifies normal and abnormal patterns based on historical data.
- Autoencoders (Neural Networks): Uses deep learning to reconstruct normal data and flag deviations.
- Use Case: Industrial IoT – Detecting vibration abnormalities in manufacturing machines to prevent failures.
2. Predictive Maintenance – Forecasting Equipment Failures
Predictive maintenance models use historical and real-time sensor data to anticipate when equipment might fail.
- Common algorithms:
- Random Forest: An ensemble learning method that predicts failures based on past data.
- LSTM (Long Short-Term Memory) Networks: A deep learning approach that excels at time-series forecasting.
- Gradient Boosting (XGBoost, LightGBM): Machine learning techniques that improve prediction accuracy over time.
- Use Case: Smart factories – Predicting motor overheating in production lines to schedule maintenance in advance.
3. AI Inference – Processing Images, Sounds, and Sensor Data Locally
AI inference enables edge devices to analyze data in real-time, rather than sending it to the cloud for processing.
- Common algorithms:
- Convolutional Neural Networks (CNNs): Used for image recognition in traffic monitoring, security cameras, and healthcare imaging.
- Recurrent Neural Networks (RNNs): Processes sequential data, such as voice recognition in smart assistants.
- YOLO (You Only Look Once): A real-time object detection model used in autonomous vehicles and surveillance systems.
- Use Case: Smart cities – AI-powered traffic cameras analyzing congestion without cloud dependency to optimize signal timing.
The Role of Edge Computing in IoT Performance
IoT devices generate vast amounts of data, ranging from temperature readings to video feeds. Transmitting this data to a centralized cloud for processing can lead to bottlenecks, delays, and higher operational costs. Edge computing addresses these challenges effectively by enabling:
- Real-Time Data Processing: Edge nodes process data instantly, allowing IoT systems to respond swiftly to changes.
- Bandwidth Optimization: Only critical data is sent to the cloud, reducing bandwidth usage.
- Enhanced Data Security: By keeping sensitive data closer to its source, edge computing minimizes risks associated with long-distance data transmission.
In IT applications, edge computing ensures seamless integration of IoT devices, enabling faster analytics, uninterrupted service, and improved user experiences.
Use Case
Smart Parking in Smart Cities
As urban populations grow, traffic congestion becomes a major challenge for city planners. Traditional traffic management systems often rely on cloud-based processing, which can lead to delays in decision-making due to network latency. Edge computing offers a real-time, decentralized solution by enabling traffic cameras and sensors to analyze data on-site, without depending on remote servers. This results in faster responses, reduced congestion, and improved urban mobility.
How Edge Computing Transforms Traffic Management
Edge-enabled traffic management systems use AI-powered cameras, sensors, and edge devices to monitor roads, intersections, and highways in real time. These systems can:
- Analyze traffic flow instantly – Cameras equipped with AI models process live video feeds to detect congestion, accidents, and unusual traffic patterns without sending data to the cloud.
- Optimize traffic signals dynamically – Based on real-time data, edge devices adjust traffic lights to ease congestion, reduce wait times, and prioritize emergency vehicles when needed.
- Detect violations and enhance safety – Edge computing helps identify traffic violations, such as running red lights or speeding, and can send alerts to law enforcement immediately.
- Reduce bandwidth and costs – Instead of transmitting all video footage to a central cloud, edge devices only send relevant insights, reducing bandwidth usage and lowering operational costs.
Example in Action
Imagine a busy downtown intersection where rush-hour traffic is causing long delays. In a traditional setup, traffic cameras capture video and send it to a remote cloud server for analysis. The system then processes the data and sends back recommendations for adjusting traffic lights—but this process can take seconds or even minutes, leading to inefficiencies.
With edge computing, AI-driven traffic cameras analyze congestion on-site and make immediate decisions. If a traffic jam starts forming, the edge system can adjust signal timings in real time to ease the bottleneck without waiting for cloud processing. Additionally, if an accident occurs, the system can instantly alert emergency responders and reroute traffic to prevent further delays.
Implementing Edge Computing: Key Steps
Implementing edge computing for IoT requires a well-thought-out strategy to ensure optimal performance. Here are the key steps:
1. Define the Use Case
Identify specific IoT applications that require real-time data processing, such as predictive maintenance, autonomous systems, or patient monitoring. Defining the use case helps determine the processing requirements and scale of deployment.
2. Select the Right Hardware
Choose edge devices and gateways capable of handling local processing efficiently. For example, an industrial setup may require rugged edge servers, while a smart home system might rely on IoT-enabled appliances with built-in processing capabilities.
3. Build a Scalable Architecture
Design a layered architecture that includes:
- IoT devices collecting data.
- Edge nodes processing data locally.
- A cloud backend for advanced analytics and long-term storage.
This hierarchy ensures efficient data flow while maintaining scalability for future growth.
4. Implement Security Measures
Security is a top priority in edge computing, where sensitive data is often processed and transmitted in real-time. To keep data safe, it’s essential to use encryption protocols that protect information as it travels between devices and the cloud, ensuring that unauthorized users can’t intercept it. Regularly updating firmware on edge devices is another key practice, as it helps patch any vulnerabilities and keep the devices secure from new threats. It’s also important to manage identities and control access to sensitive systems. By using strong authentication and authorization methods, you can ensure that only trusted users and devices have access to critical data. These proactive steps help protect edge computing systems from cyberattacks and keep everything running securely. Edge computing relies on strong encryption to secure real-time data transmission. TLS protects communication between devices and the cloud, while AES-256 encrypts stored data. IPSec ensures secure network traffic, and MQTT with TLS/DTLS secures IoT messaging. Zero Trust Security (ZTS) enforces strict identity-based access. Together, these protocols safeguard edge systems from cyber threats.
5. Leverage AI and Machine Learning
Integrate AI algorithms at the edge to enable predictive analytics, anomaly detection, and intelligent decision-making. For example, smart cameras equipped with AI can detect security breaches and trigger immediate alerts. The example of smart cameras equipped with AI detecting security breaches falls under computer vision and image processing.
Benefits of Edge Computing in IT
Faster Response Times
By processing data locally, edge computing significantly helps in reducing latency. This is crucial for applications like autonomous vehicles, where split-second decisions can mean the difference between safety and disaster.
Cost Efficiency
Transmitting large volumes of data to the cloud can be expensive, especially for high-bandwidth applications like video surveillance. Edge computing reduces data transfer costs by processing most data locally.
Improved Reliability
Edge systems can function independently of the cloud, ensuring continued operation during network outages. This makes them ideal for mission-critical applications in industrial and healthcare settings.
Applications of Edge Computing in IoT
Edge computing has revolutionized various industries by enabling IoT devices to perform more efficiently.
Smart Cities
In smart cities, edge-enabled systems optimize traffic management, energy usage, and public safety. For instance, traffic cameras equipped with edge computing can analyze congestion patterns in real-time, improving traffic flow.
Healthcare
Edge computing empowers healthcare devices to monitor patients continuously and respond to emergencies instantly. A wearable device with edge capabilities can detect irregular heart rates and alert medical personnel in real time.
Industrial Automation
Factories use edge computing to monitor machinery, predict failures, and reduce downtime. Real-time insights ensure smoother operations and cost savings.
Challenges and How to Overcome Them
While edge computing is a game-changer for IoT, it comes with its own set of challenges. Here’s how to tackle them effectively:
1. Hardware Limitations – Choosing the Right Edge Hardware
Edge devices don’t have the same power as cloud servers, so picking the right hardware for the job is crucial. For AI-powered tasks like traffic monitoring or security cameras, NVIDIA Jetson AGX Orin provides high-speed processing for video analytics. In industrial automation, Raspberry Pi Compute Module 4 or Rockchip RK3568-based devices offer real-time processing with low power consumption. The key is to match your hardware with your needs—AI-heavy applications require AI accelerators, while lightweight tasks can run on power-efficient processors.
Benchmarks for Selecting Edge Hardware
When choosing edge computing hardware, consider the following key benchmarks:
- Compute Performance (TOPS/FLOPS) – Higher TOPS (Tera Operations Per Second) or FLOPS (Floating Point Operations Per Second) indicates better AI inference performance.
- Power Consumption (Wattage) – Power efficiency is crucial for battery-operated or remote IoT devices.
- Memory (RAM & Storage) – More RAM and storage improve real-time data processing and caching.
- Connectivity & Interfaces – Supports required interfaces like Ethernet, USB, PCIe, and wireless (Wi-Fi, 5G, LoRa) for smooth communication.
- Scalability & Cost – Balances performance with affordability for large-scale deployments.
2. Connectivity Issues – Ensuring Offline Functionality
Network failures can disrupt real-time processing, so edge devices need to keep working even when the internet is down. One way to do this is by enabling offline processing, where devices store and analyze data locally before syncing with the cloud when the connection is restored. For example, Tesla’s Autopilot processes data on-board, ensuring it can still make driving decisions even without an internet connection.
3. Data Security Concerns – Implementing End-to-End Encryption
Because edge computing distributes data across multiple locations, it’s more vulnerable to cyber threats. The best way to secure it is by encrypting data both in transit and at rest using AES-256 or TLS encryption. This ensures that even if hackers intercept the data, they can’t read it. Pairing this with secure access protocols and regular security audits helps keep systems locked down and protected.
Future of Edge Computing in IT
The future of edge computing in IT is exciting, especially with 5G making connections faster and more reliable. New ideas like running serverless apps at the edge and using blockchain to share data safely are changing how edge systems work. These improvements will make edge computing easier to grow, faster, and safer.
Conclusion
Edge computing is reshaping the way IoT devices function in IT, providing faster processing, enhanced security, and cost-effective solutions. By processing data closer to its source, edge computing unlocks new possibilities for industries ranging from healthcare to manufacturing.
Organizations looking to optimize IoT performance should embrace edge computing as a strategic investment. With the right implementation strategies, businesses can achieve real-time insights, improve efficiency, and stay ahead in the competitive IT landscape.
References
- Edge Computing for Iot –https://www.researchgate.net/publication/378321885_Edge_Computing_for_IoT
- What is edge computing and how to use it. https://www.computer.org/publications/tech-news/trends/edge-computing-in-iot
- Concept and contribution of Edge computing : https://www.ijcna.org/abstract.php?id=645