- Jintu K Joseph
- August 20, 2025
Understanding Security and Safety in Modern SoC Designs | Part 3
This article is Part 3 of a 3-part blog series on Security and Safety in Modern SoC Designs. If you haven’t read Part 1 and 2 yet, check it out here:
Part 1: Understanding Security and Safety in Modern SoC Designs
Part 2: Understanding Security and Safety in Modern SoC Designs
1. Case Studies: Security-Centric IPs in SoCs
In modern SoCs, security is often built using dedicated IP (Intellectual Property) blocks. These are reusable components or processor cores that come with built-in features to help protect the chip from attacks. Here are some well-known examples of security-focused IPs and how they are used in real-world applications.
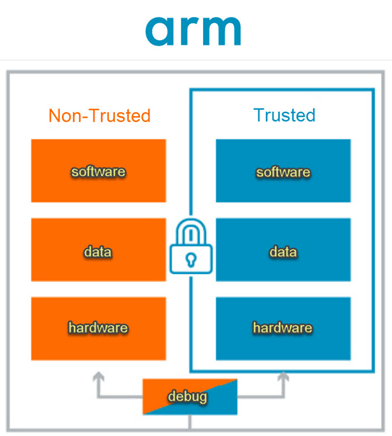
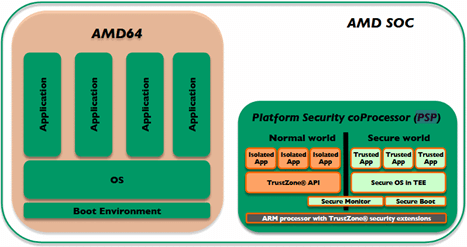
Arm TrustZone: Arm TrustZone is a popular security feature available in many Arm-based SoCs. It creates two separate worlds inside a single chip—one for normal tasks and another for secure operations. For example, apps, games, and general software run in the “normal world,” while cryptographic functions, secure payments, and biometric data processing happen in the “secure world.” This separation helps prevent attackers from accessing sensitive data, even if the normal world is compromised. TrustZone is widely used in smartphones, wearables, and automotive systems.
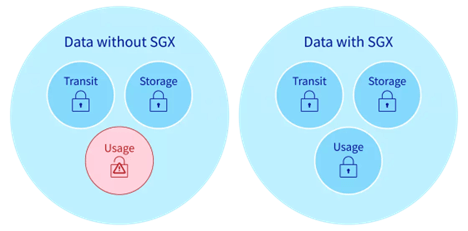
Intel SGX (Software Guard Extensions): Intel SGX allows applications to create secure memory areas called “enclaves” that are isolated from the rest of the system, even from the operating system and hypervisor. Sensitive code and data can be stored in these enclaves, making it very difficult for attackers to read or tamper with them. SGX is commonly used in cloud computing and enterprise systems to protect confidential information even if the broader system is compromised.
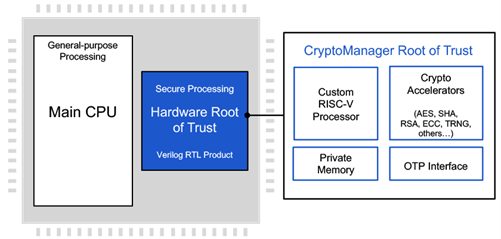
Rambus RT Cores: Rambus offers a range of secure processor cores, including the RT series, designed for high-assurance applications. These cores support Trusted Execution Environments (TEEs), Secure Boot, and real-time cryptographic processing. They are used in applications where both performance and security are critical, such as automotive ECUs (Electronic Control Units), industrial systems, and IoT devices. Rambus RT cores are built with tamper resistance and runtime security monitoring in mind.
NVIDIA, AMD, and Apple SoC Security Examples: Leading technology companies have also developed their security features tailored to their specific platforms:
- NVIDIA SoCs include secure boot, hardware crypto engines, and isolated security processors for handling trusted tasks in automotive and AI edge devices.
- AMD’s Platform Security Processor (PSP) manages firmware verification, key storage, and secure boot on their Ryzen and EPYC processors.
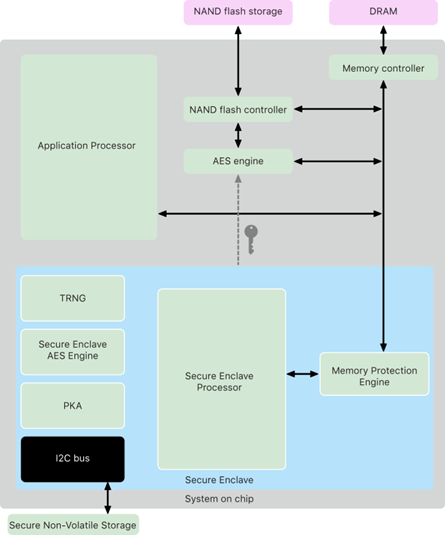
Apple’s Secure Enclave is a dedicated subsystem for sensitive tasks like fingerprint and facial recognition, password storage, and secure payments. It operates independently of the main processor, increasing protection even in the event of system compromise.
- Arm Cortex-M33: This is a popular microcontroller core used in small, power-efficient devices. It supports Arm TrustZone, which creates a secure world and a normal world within the same chip, allowing sensitive tasks to run separately from general tasks. It also includes cryptographic acceleration to speed up secure communication and has Secure Flash support to protect firmware from being read or modified. These features make it ideal for IoT applications and smart metering systems, where device identity and secure updates are essential.
- Arm Cortex-A78: The Cortex-A78 is a high-performance core designed for mobile phones and edge computing devices. It comes with built-in cryptographic extensions to improve the speed and strength of encryption operations. It also supports PSA (Platform Security Architecture) compliance, which helps standardise security features across different devices. With Secure Boot and other protection mechanisms, it is well suited for smartphones, tablets, and AI-powered edge devices that process sensitive user data.
- Arm Cortex-R5: This processor is built for real-time systems where safety and reliability are key. It supports real-time TrustZone, allowing secure and non-secure tasks to run simultaneously with predictable timing. ECC (Error-Correcting Code) memory support adds another layer of safety by detecting and fixing memory errors. It also includes a Memory Protection Unit (MPU) to restrict access to different memory regions. These features are especially important in automotive Advanced Driver Assistance Systems (ADAS) and industrial automation, where precision and fault tolerance are crucial.
These IPs provide the building blocks for designing secure and reliable SoCs. By selecting the right combination of IPs, designers can create chips that meet the unique security requirements of various industries.
2. SoC Boot Flow and Anti-Reverse Engineering Measures
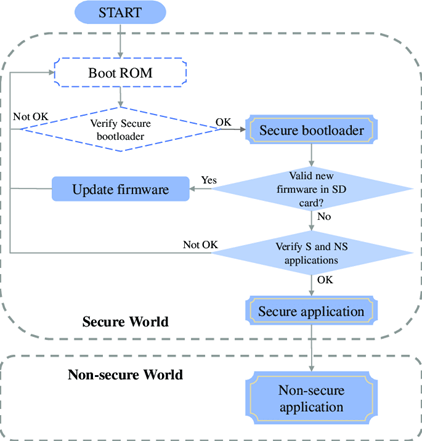
To ensure that a System-on-Chip (SoC) starts up securely and cannot be taken over by malicious software, designers implement a secure boot flow. This is a step-by-step process that checks the trustworthiness of each software component before it runs. Think of it as a series of locked doors—each one only opens if the right key is presented.
- The process begins with the Boot ROM, which is a small piece of code stored permanently on the chip. Because it cannot be changed, it acts as the foundation of trust. The Boot ROM performs the first check: it verifies the digital signature of the next software component, which is usually the bootloader.
- Digital signature verification works like a seal of authenticity. The bootloader must be signed by a trusted source, and the Boot ROM uses cryptographic keys to verify that the signature is valid. If the signature doesn’t match, the chip will refuse to run the bootloader, stopping the startup process right there.
- Once verified, the bootloader performs a similar check on the operating system or firmware. This layered verification process ensures that only trusted software is allowed to run at each stage. It also prevents attackers from sneaking in malicious software during startup.
- The cryptographic keys used for verification are stored in special parts of the chip called OTP (One-Time Programmable) memory or eFuses. These areas can be written only once, making it nearly impossible for attackers to change the keys later.
- To further strengthen security, many SoCs implement anti-rollback mechanisms. These prevent an attacker from installing an older version of the firmware that might have known vulnerabilities. The chip keeps track of the firmware version, and if someone tries to install an outdated version, the system will block it.
- All of these steps work together to prevent malware from hijacking the boot process. They ensure that every part of the software that runs after power-on is verified and trusted, making it much harder for attackers to take control of the device.
In addition, anti-reverse engineering techniques—like code obfuscation, tamper-proofing, and secure key storage—are used to make it difficult for attackers to study the chip and understand how to exploit it. These measures protect both the intellectual property of the chip designer and the security of the end-user.
3. Security Breaches in SoCs: Real Incidents
Real-world security breaches serve as important reminders of how even small vulnerabilities in a system-on-chip (SoC) can lead to major consequences. Here are a few notable incidents that show the wide variety of risks—ranging from natural phenomena to sophisticated attacks—that SoCs can face.
- Belgian SEU Election Incident: In a widely reported case in Belgium, a voting machine produced an unexpected result: a candidate received more votes than there were eligible voters. Upon investigation, it was discovered that a single event upset (SEU)—a bit-flip caused by cosmic rays—had altered the stored data in memory. Though not a malicious attack, this incident highlighted how vulnerable electronics can be to environmental factors and the importance of fault detection in critical systems.
- Spearphone Attack: Researchers demonstrated an attack called Spearphone, where the motion sensors (accelerometers) in a smartphone were used to pick up vibrations from the device’s speaker. These vibrations could be analysed to reconstruct the audio being played, effectively leaking private conversations or media. The attack showed how components not traditionally associated with security (like sensors) can be exploited as side channels for data theft.
- Side-Channel and Rowhammer Attacks: Side-channel attacks, such as power analysis or timing attacks, continue to pose threats by allowing attackers to infer secret data without directly accessing it. Another well-known threat is the Rowhammer attack, where repeated access to specific memory rows causes bit-flips in adjacent rows. This type of vulnerability can be used to gain unauthorised access or change system behaviour, especially if no error correction is in place.
Lessons Learned: These incidents underline several important points:
- Secure every interface: Even sensors, debug ports, or seemingly harmless peripherals can become points of attack if not properly protected.
- Protect against both physical and logical threats: Threats may come from environmental conditions, direct hardware tampering, or remote software exploits.
- Update and audit firmware regularly: Firmware bugs are often discovered after devices are in use. Regular updates and code audits help close security holes and protect users over the device’s lifetime.
By studying these real-world failures and attacks, engineers and security experts can better anticipate risks and design more resilient SoCs.
4. Future Trends in SoC Security and Safety
As technology continues to evolve, so do the challenges and solutions in securing System-on-Chip (SoC) designs. New computing models, advanced threats, and emerging applications are reshaping the security and safety landscape. To keep up, future SoCs will need to adopt cutting-edge technologies that go beyond today’s standards. Below are some key trends expected to shape the next generation of secure and safe SoCs.
- Post-Quantum Cryptography in SoCs (Making Chips Safe from Future Computers): Today’s encryption methods—like RSA and ECC—are strong, but future quantum computers might be powerful enough to break them. Post-Quantum Cryptography (PQC) means building new encryption systems that even quantum computers can’t break. SoC designers are now preparing for that future by planning to add new types of encryption directly into the hardware. This ensures that data on your phone, car, or connected device stays secure, even years from now when quantum technology becomes real. [Think of it as upgrading your locks today to protect against the smarter thieves of tomorrow.]
- AI-Based Runtime Security Agents (Smart Security That Learns as It Works): Chips are becoming so advanced that they can monitor themselves using artificial intelligence (AI). These AI-based “security agents” learn what normal behaviour looks like, and if something strange happens—like a hidden bug, data leak, or unusual app—they can quickly spot it. Even better, AI doesn’t rely on fixed rules. It can adapt and protect the chip from new threats that no one knew about when the chip was made.[It’s like a watchdog that learns what’s normal and immediately barks when something’s off.]
- Digital Twins for Safety Simulation (Testing Chips in Virtual Worlds): A digital twin is a computer-made version of a real chip. Engineers use this “twin” to run experiments and test how the real chip would react to things like errors, attacks, or high temperatures, without damaging the actual chip. This helps designers fix problems early and make chips safer and more reliable before they are built and used in products like cars or medical devices. A digital twin is a real-time, virtual copy of a physical chip (or system) that runs alongside the real thing. (Like practising on a virtual car crash dummy before building the real car.)
- Quantum Side-Channel Resistance (Blocking Sneaky Listening Tricks): Quantum technology might not just break encryption—it could also be used to “listen in” on a chip’s tiny signals, like its electrical noise or power usage, to steal secrets. To stop this, future SoCs will use shielding, randomised power signals, and clever circuit design so that no useful information can be stolen this way. [Think of it like covering a window with blinds so no one can peek through.]
- Fully Homomorphic Encryption in Hardware (Keeping Data Secret Even While Using It): Normally, if a chip wants to use some data (like your photo or medical info), it has to decrypt it first, which means there’s a small risk someone could steal it. But fully homomorphic encryption (FHE) is special: it lets the chip use the data while it’s still encrypted, without ever unlocking it! Though this kind of processing is slow today, researchers are working on making it faster by adding special hardware. In the future, this could make very private tasks—like medical processing, online voting, or cloud services—much more secure. [It’s like doing math on a locked box of numbers without ever opening the box.]
SoCs of the future won’t just be fast—they will need to be smart, secure, and ready for challenges we haven’t even seen yet. From AI that guards your chip to encryption that even future quantum computers can’t crack, these technologies are building a safer tomorrow for everything from phones to cars to hospitals.