- Jintu K Joseph
- July 23, 2025
Understanding Security and Safety in Modern SoC Designs | Part 1
System-on-Chip (SoC) technologies have revolutionised modern electronics by integrating diverse functions, such as CPUs, GPUs, AI engines, and communication modules, into a single chip. These chips now power everything from mobile phones to automotive safety systems. However, this high degree of integration also exposes SoCs to a broader range of security vulnerabilities and safety risks. Addressing both functional security (against malicious attacks) and functional safety (against accidental faults) is now a cornerstone of reliable and resilient SoC design.
In this blog series, we will explore:
- Mapping Trust in the SoC Lifecycle — Where to Focus Security Efforts
- The growing attack surface of SoCs
- Threats like Hardware Trojans
- Understanding Side-Channel Attacks in SoCs
- Comparing Surface-Level Attacks and Side-Channel Attacks in SoCs
- Security Mechanisms for Surface-Level Attack Prevention
- Understanding Hardware Trojans in SoCs
- Analog and Mixed-Signal Security Challenges
- Detection and Mitigation Strategies in SoCs
- RISC-V vs. CISC: Security and Safety Considerations
- Functional Safety and Security in SoCs
- Role of Verification Engineers in SoC Security
- Case Studies: Security-Centric IPs in SoCs
- SoC Boot Flow and Anti-Reverse Engineering Measures
- Security Breaches in SoCs: Real Incidents
- Future Trends in SoC Security and Safety
Let’s begin our deep dive into securing the foundations of smart systems.
1. Mapping Trust in the SoC Lifecycle — Where to Focus Security Efforts
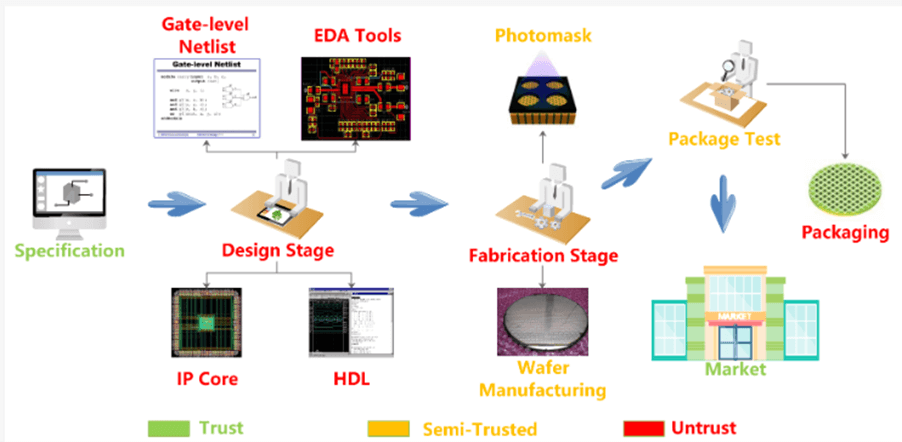
Modern SoC designs involve multiple stages, each with different levels of exposure to potential tampering or malicious modification. According to the MDPI survey on Hardware Trojans, evaluating the credibility or trustworthiness of each stage in the chip development lifecycle is essential to identifying where the greatest security risks lie.
The process begins with the specification stage, where the intended behaviour and performance of the chip are defined. This phase is considered trustworthy because it does not involve any direct implementation or manipulation of the hardware. Similarly, the final testing and market release stages are also viewed as trusted because they involve verifying chip functionality and packaging the final product, without the authority to modify the hardware design.
In contrast, the design and synthesis stages are marked as semi-trusted or untrusted. These phases often involve using third-party Intellectual Property (IP) cores, external Electronic Design Automation (EDA) tools, and pre-built standard cells. Each of these components introduces the possibility of backdoors or hidden logic being inserted into the chip. Because these tools and IPs may come from different vendors worldwide, it’s difficult to verify their integrity fully.
Even more critical is the fabrication stage, where the chip design is transformed into a physical product. This step involves generating photomasks, wafer fabrication, and die packaging—all of which can be outsourced to foundries in different geographic regions. These foundries may not be under the direct control of the chip designers, which creates a serious vulnerability. Suppose any part of the fabrication process is compromised. In that case, malicious modifications such as Hardware Trojans can be embedded at a level that is nearly impossible to detect using traditional post-manufacturing tests.
To visualise this concept, the MDPI paper categorises the lifecycle stages using a colour-coded model:
- Green (Trusted): Specification, final verification, and post-silicon testing.
- Yellow (Partially Trusted): IP sourcing, EDA tools, and logic synthesis—stages where the design can still be modified, but with some oversight.
- Red (Untrusted): Mask generation, fabrication, and packaging—these phases have the most authority and lowest transparency, making them the most vulnerable.
This layered trust model helps SoC developers focus their security efforts effectively. For example, advanced verification techniques, such as formal analysis and golden model comparison, should be heavily applied during design and synthesis. Likewise, supply chain validation, secure foundry partnerships, and chip fingerprinting may be essential at the fabrication level.
Understanding which stages of the chip lifecycle can and cannot be trusted allows developers to plan better defences and reduce the risk of malicious interference. This approach is not only useful for building secure hardware, it is critical for ensuring long-term credibility in high-stakes applications like defence, healthcare, and autonomous vehicles.
Modern SoCs are rarely developed entirely in one place. A single chip might be designed in the United States, fabricated in Taiwan, assembled in Malaysia, and tested in China. Along the way, it may incorporate third-party IPs, EDA tools, standard cells, and testing services from vendors all over the world. This opens the door for various threats, such as:
- Hardware Trojans inserted during design or fabrication
- Counterfeit chips or components
- Modified test or packaging processes
- Leakage of sensitive IP or design data
Trust Models Across Lifecycle Stages: To manage these risks, developers use trust models that classify each stage of the IC lifecycle based on its level of control and risk. For example:
- Trusted stages like specification definition and final testing are considered low risk because they do not modify the chip’s internal structure.
- Semi-trusted stages like IP integration and EDA tool use have a moderate risk because they influence design, but may still be reviewed.
- Untrusted stages like fabrication and packaging are high risk, especially when outsourced, because malicious changes can be made at the physical level.
Understanding which stages are most vulnerable helps guide security investments and testing efforts.
- Hardware Fingerprinting and Authentication: To verify that a chip hasn’t been tampered with or swapped for a counterfeit, techniques like hardware fingerprinting are used. Every chip has slight variations due to manufacturing imperfections. These tiny differences can be measured and used as a kind of digital “fingerprint” for authentication. This ensures that only genuine and authorised chips are used in secure systems.
- Blockchain and Secure Provenance: Blockchain technology is also being explored to track the provenance (origin and journey) of chips through the supply chain. Each transaction or movement of the chip—from factory to shipping to deployment—can be recorded on a tamper-proof blockchain ledger. This improves transparency, helps detect tampering, and builds trust between partners.
- Tamper Detection and Self-Destruction Logic: Some chips are built with tamper detection circuits that can sense when someone is trying to physically probe or alter them. These sensors monitor voltage levels, temperature, or package opening. If tampering is detected, the chip can activate a response such as erasing secure keys, disabling critical functions, or even self-destructing certain internal elements to prevent information theft.
In summary, securing the supply chain is just as important as securing the chip itself. By using a combination of risk modelling, fingerprinting, tamper detection, and emerging technologies like blockchain, designers can ensure that every chip in the field is both genuine and secure.
2. SoC Complexity and the Role of IPs in Security
Modern SoCs integrate a vast range of IP cores, including CPU/GPU cores, memory interfaces, AI accelerators, DSPs, security modules, and more. This diversity adds design complexity, especially when handling third-party IPs, customising cores for application-specific needs, ensuring reliable interaction between blocks, and securing the entire system from potential threats. Managing third-party IPs from various vendors can be challenging because each vendor may follow different design and security practices. Some IPs might be well-tested and documented, while others may lack transparency or adequate support. Integrating these IPs into a single cohesive SoC requires extra effort to validate compatibility and trustworthiness. Customising IPs for specific applications is often necessary to meet unique requirements, such as performance tuning in automotive chips or power-saving in wearable devices. However, customisation introduces risks, as modifications can introduce unforeseen bugs or make future maintenance harder. It also demands additional engineering time and resources. Verifying interactions across hundreds of blocks is complex because even if each IP core functions correctly on its own, unexpected issues can arise when they interact. Timing mismatches, data corruption, or protocol mismatches can cause failures that are difficult to debug. Comprehensive verification requires the use of sophisticated simulation, emulation, and formal methods. Securing the SoC against untrusted components is crucial, especially when incorporating third-party IPs or outsourcing parts of the design. Malicious modifications (e.g., hardware Trojans) can be introduced during integration. Designers must ensure that each IP is validated for integrity, and security boundaries are enforced at both the hardware and software levels.
Key Challenges:
- Interconnect Complexity: With numerous cores communicating simultaneously over shared buses or networks-on-chip (NoCs), ensuring efficient, reliable, and secure data flow becomes a massive task. Poorly managed interconnects can become bottlenecks or security vulnerabilities.
- Customisation Tradeoffs (Power, Performance, Area): Optimising the SoC for power, performance, and area often involves tradeoffs. Enhancing one aspect might compromise another. Designers must carefully balance these metrics while ensuring functional integrity and security.
- Extensive Verification Requirements: Due to the sheer number of components and interactions, SoC verification is time-consuming and resource-intensive. Missed edge cases during verification can result in serious bugs post-silicon, affecting product reliability and safety.
- Supply Chain Security Risks: Relying on global supply chains for IP, tools, and fabrication opens doors to tampering, IP theft, or counterfeit components. Ensuring the security and authenticity of every supply chain element is essential to prevent long-term risks.
3. Attack Surfaces in SoCs
Every interface, memory segment, and peripheral in an SoC is a potential attack vector. Below are key areas where attackers may target SoCs and why each one is important:
- Hardware Interfaces (JTAG, UART): These are ports built into the chip to help developers test and debug the system during development. JTAG and UART can give deep access to the chip’s internal functions. If these ports are not disabled or protected in the final product, attackers can use them to take control of the device, read sensitive data, or change how the chip works.
- Firmware & Boot Process: Firmware is the first code that runs when a device powers on. If attackers can replace or modify the firmware, they can gain complete control over the system before any security checks are applied. Secure Boot helps protect against this by verifying that only trusted firmware can run, but if not properly implemented, it becomes a major vulnerability.
- Shared Memory & Side-Channel Attacks: In an SoC, multiple parts (like the CPU, GPU, and peripherals) often share memory access. If one component can read what another is doing, sensitive information can be leaked. Additionally, side-channel attacks look at indirect clues like power usage or timing to guess what data is being processed—such as secret encryption keys—without needing direct access.
- Untrusted IP Cores: SoCs often include third-party components, called IP cores, which may not be fully transparent or secure. If any of these cores contain bugs or malicious logic, they can become backdoors into the system. It’s difficult to inspect every third-party component, so they remain a big security risk.
- On-Chip Networks (NoC): Inside an SoC, components communicate through internal networks known as NoC (Network-on-Chip). If attackers can tap into this network, they may be able to intercept or manipulate data being exchanged. Without proper isolation and access control, the NoC can become a path for attacks to spread across the chip.
- External Connectivity (USB, Wi-Fi, etc.): Modern SoCs connect to the outside world through many interfaces. These include wired connections like USB and HDMI, or wireless ones like Wi-Fi and Bluetooth. These connections are useful but also provide entry points for attackers. For example, a malicious USB stick can compromise a device, or a vulnerability in the Wi-Fi stack can be exploited remotely.
- Operating System Drivers & Kernel Modules: The software that talks to hardware—like device drivers and kernel modules—runs with high privileges. If this software has bugs, attackers can exploit them to gain control over the system. Since these components are essential to SoC operation, they must be carefully written and regularly updated.
- Supply Chain Tampering: SoCs go through a long production process involving many different companies and tools. If someone tampers with the design, tools, or manufacturing process—intentionally or unintentionally—they can introduce hidden threats, such as hardware Trojans or counterfeit parts. These risks are hard to detect after the chip is made and can stay hidden for years.
- Each of these areas must be secured through a combination of hardware protections, cryptographic measures, and good design practices.
Each must be secured through hardware controls, cryptographic protections, and physical design measures.
4. Understanding Side-Channel Attacks in SoCs
A side-channel attack is a unique and clever form of security threat in the world of System-on-Chip (SoC) design. Unlike traditional attacks that try to break into software through bugs or weaknesses in code, side-channel attacks take a completely different route. They focus on the tiny clues a chip unintentionally gives away while it is working—clues that are not part of its actual output.
Imagine a secure SoC performing encryption. It might seem safe because it uses strong algorithms like AES or RSA. But what if someone could measure how much power the chip uses while encrypting? Or, how long does it take to finish certain operations? Or even the small electromagnetic waves it emits? These are all examples of side channels—paths that leak sensitive information, even when the chip itself appears perfectly secure.
For example, when encrypting different data, the chip might consume slightly different amounts of power. By observing these small changes over many encryption operations, an attacker can start piecing together what’s going on inside. Eventually, they might be able to figure out the secret key used in the encryption. The same goes for timing attacks—if some operations take longer than others, depending on the data, that timing difference can leak secrets too.
Compared to other kinds of security threats, side-channel attacks are especially dangerous because they do not require breaking through software protections. A typical software attack might try to exploit a bug in the operating system or an app, but a side-channel attack just watches the physical behaviour of the chip. It doesn’t need to inject any code or trigger any alarms, making it very stealthy and hard to detect.
This makes side-channel attacks a serious concern in sensitive devices, like payment terminals, secure communications systems, or even smartphones. Since SoCs are tightly packed with many components, and often share memory or buses between blocks, the risk of leaking information through side channels becomes even higher.
To defend against such attacks, designers must go beyond writing secure software. They need to build hardware that avoids giving away these indirect clues. This includes techniques like using constant-time operations, adding random noise to power usage, shielding circuits from electromagnetic analysis, and isolating sensitive parts of the chip.
In summary, side-channel attacks are a kind of silent spy—they don’t break in, but they listen carefully. And in the world of SoCs, where everything is closely packed and highly optimised, listening is sometimes all it takes to uncover a secret.
5. Comparing Surface-Level Attacks and Side-Channel Attacks in SoCs
In the context of SoC (System-on-Chip) security, it’s important to understand the difference between the two major categories of attacks: surface-level attacks and side-channel attacks. Although both are threats to the system, they differ significantly in how they are carried out and what they target.
Surface-level attacks are more direct and usually involve exploiting a vulnerability in the SoC’s software or hardware interfaces. These could include bugs in the firmware, insecure boot processes, or exposed communication ports like JTAG or USB. For example, if an attacker finds a flaw in the way the firmware handles updates, they might upload a malicious version that gives them control over the device. Surface-level attacks often target areas that are already meant to interact with users or developers, but which haven’t been properly secured.
Side-channel attacks, on the other hand, are more subtle and indirect. Instead of targeting flaws in code or open interfaces, these attacks observe the physical behaviour of the chip—such as power consumption, timing, or electromagnetic emissions—to extract sensitive information. For example, by measuring how long it takes a chip to encrypt data, an attacker might infer secret encryption keys. These attacks are like digital eavesdropping, using clues the chip accidentally gives away.
The key difference lies in how the information is obtained. Surface-level attacks exploit weaknesses in what the chip does; side-channel attacks exploit how the chip does it. Surface-level attacks are usually easier to launch if software bugs or misconfigurations exist, while side-channel attacks require more effort, special equipment, and sometimes physical access—but they can bypass even well-written code.
Another difference is in detection. Surface-level attacks may leave traces in logs or cause visible errors, making them easier to detect. Side-channel attacks, being passive and stealthy, are much harder to notice and can go undetected for long periods.
In summary, both types of attacks are serious threats. Surface-level attacks are like picking a lock to get in; side-channel attacks are like listening through the walls to learn what’s inside. A secure SoC must defend against both.
This article is Part 1 of a 3-part blog series on Security and Safety in Modern SoC Designs. Explore the full series:
Part 2: Understanding Security and Safety in Modern SoC Designs
Part 3: Understanding Security and Safety in Modern SoC Designs